*Flipper Zero has entered the LEGO Store*
These days, I went to visit for the first time the very crowded and highly awaited LEGO store in Dublin city centre. I was very impressed by the amount of new merch with different IPs and brands that LEGO tied to over the years. They even made a Brian's Nissan Skyline from Fast & Furious set!
The most interesting thing that captured my curiosity was the possibility to create your own minifigure by customizing the upper body of the LEGO character and then adding your own favourite legs, heads and accessories. They call this service LEGO Minifigure Factory. Everyone among my acquaintances has been talking about this thing, so to compensate this FOMO, I thought to give it a try.
The experience works so that: you will need to buy a little box behind the counter first, the retailer will then hand it over to you for the price of €12. Finally, you will have to place this box on a NFC reader area (blue rectangle in the last picture) which will activate the UI for creating the minifigure. After choosing various styles and tweaking the chest/back of the minifigure, you will send it over to the main printer, where a person will inspect the design and print it for you. Quick and easy, the results were really impressive!
Once home, I decided to snoop around the NFC tag inside the little minifigure box with my newly acquired Flipper Zero. The poor thing has been catching dust for months, mainly because I've been focused on other projects and totally not because of laziness. Anyways, firing up the NFC reader it immediately detected a Mifare Ultralight 11, with 20/20 pages read, nice! I thought, thank god it's not a DESfire, so maybe I could actually do something with this. After opening up the payload, I noticed various data about the tag, including a default password set to FF FF FF FF.
I thought OK, now this thing was easy to decode, my second plan was: can I buy a new box, clone the tag with the Flipper and then use it on the Figure Factory computer? Went a second time to the LEGO store, very sneaky fired up the Flipper once again, proceeded to read a newly purchased box and then emulated the tag by placing it onto the NFC reader area. YES, it just worked! I was able to clone the box and start customizing the minifigure.
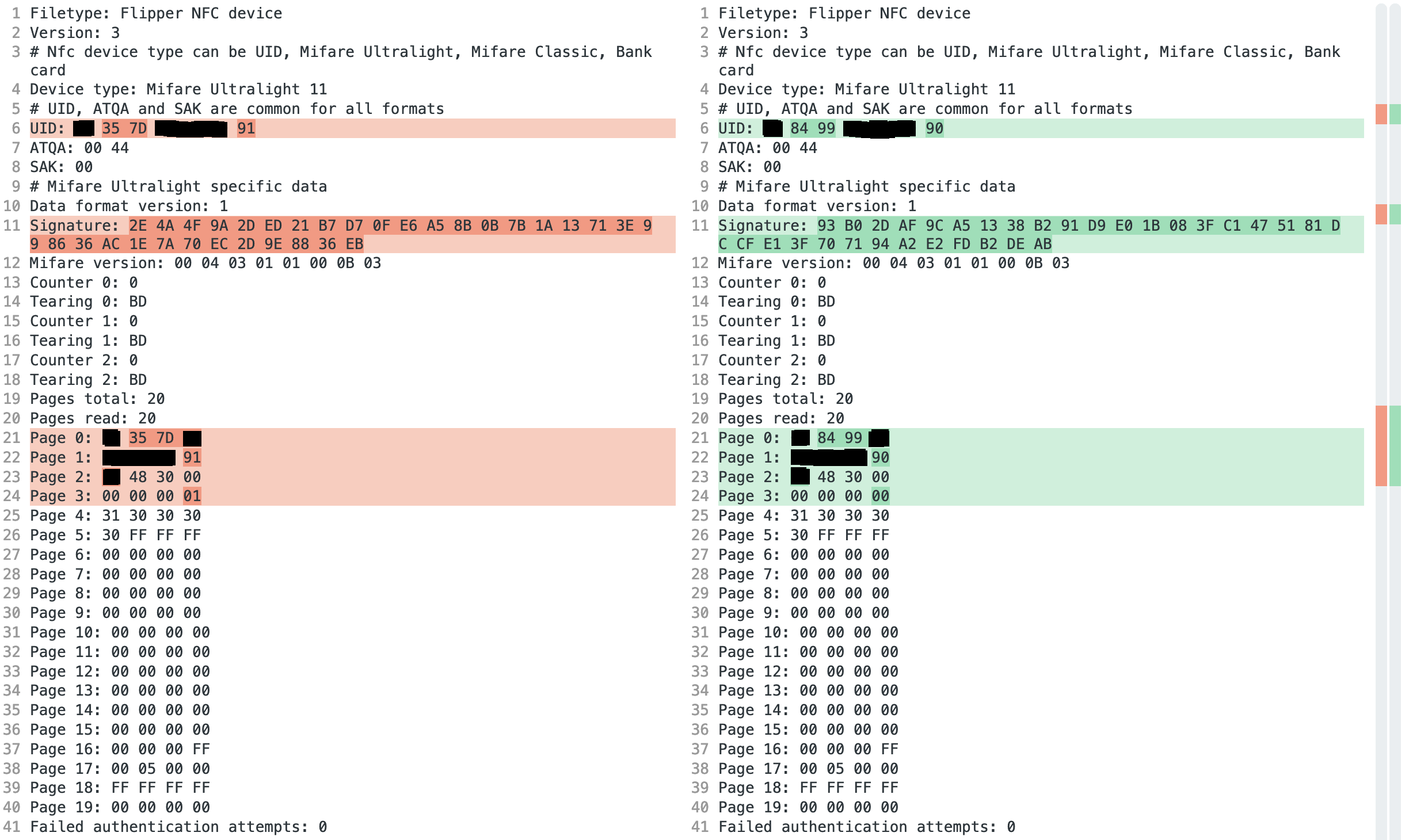
Back home, I decided to open up the second payload and diffcheck the two boxes to spot differences. Keep in mind the second box (that was legally purchased) wasn't used but only emulated with the Flipper!
Needless to say, the two things were almost identical, except for a few bytes of the UIDs and the 32 byte signature. Fortunately, the password was still the default one.
Thanks to the Ultralight EV1 datasheet, I could interpret the few bytes in the first five pages.
I started brainstorming if there was a way to randomly generate and emulate new boxes. My biggest concern was of course the signature, what if the computer validated the signature and blocked me from accessing the UI? I took my chances and wrote a stupid simple 💎 Ruby script which generates new random LEGO box payloads by looking at the bytes of the boxes I already used.
I randomly generated the byte 1, byte 2 and last digit of byte 6 in the UID. Afterward, I generated the check byte 0 and check byte 1 (according to the 8.5.1 UID/serial number of the datasheet). Finally, a 32 byte signature.
One small detail I noticed from the second unused box (because it was cloned with Flipper) was: on page 03h the last bit of the fourth byte was set to 0, while it was 1 in the first box payload. My best guess was that on activation, the minifigure computer automatically wrote over this bit to support the anti-tearing feature. So, I decided to make my payloads with the bit set to 0 to replicate an unused box.
After making a bunch of payloads using the script, 6 with a random signature and 6 with a reused signature (from my previous boxes), I was ready to go to the store once again and give this a go.
I purchased a third box, to have a clean conscience before doing my test :) and proceeded to emulate my randomly generated boxes *drum rolls* … YES it worked!
I immediately left the machine asking the retailer to stop the process before I could finish the print.
In the end, the validation did not take into consideration neither the signature nor any sort of password encoded in the payload, so my conclusion is: the check must be performed only on the UID range. The one scenario I still haven't tested is to check if I can re-use the same UID/payload from a previously activated box.
Maybe the OTP bytes on page 03h are checked to prevent re-using the same box? who knows…
Flipper Zero truly is a great tool to tinker with, but (impostor syndrome moment) I do feel it is a bit wasted on me as I still need to learn a lot about the protocols and technologies that it can analyze. Nonetheless, this was an extremely fun project to work on and hopefully learned something about the Mifare technology.